Cyber threats are more advanced, persistent, and costly than ever before.
Traditional security approaches are no longer enough.
Our SOC-as-a-Service (SOCaaS) delivers continuous monitoring, rapid detection,
and intelligent response — all powered by AI, automation, and expert analysis.
We help enterprises secure their digital assets, reduce exposure, and achieve compliance with a
future-ready SOC model designed for resilience and scalability.
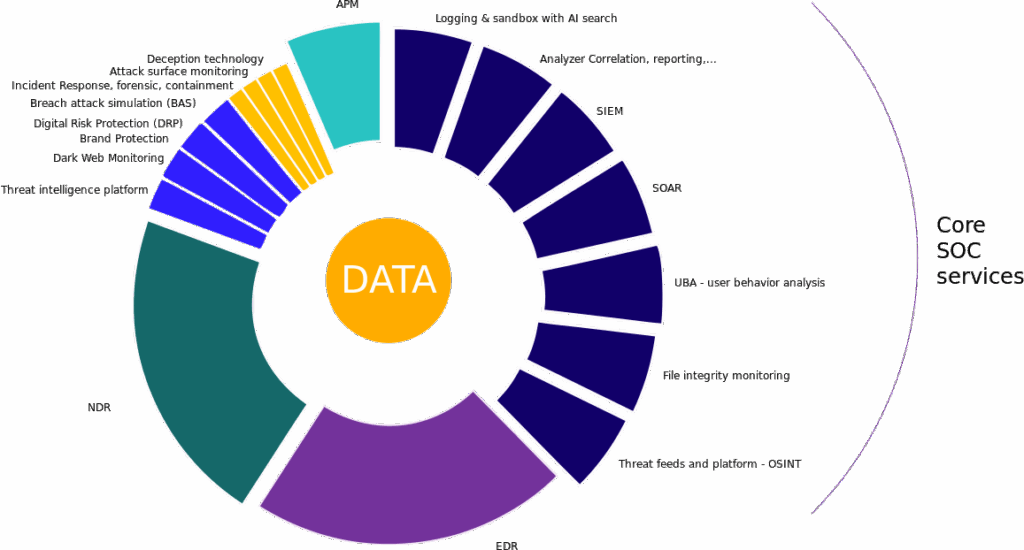
Our Core SOC Services bring together advanced technologies, continuous monitoring, and expert-led response into a single integrated ecosystem.
From proactive deception and attack surface monitoring to AI-powered analytics and automated incident response,
we deliver end-to-end visibility and control over your entire security landscape.
By combining threat intelligence, automation, and forensic capabilities, our SOC provides:
This holistic approach ensures that your organization stays protected, resilient, and prepared against both known and emerging cyber threats —
a 360° defence ecosystem tailored to modern enterprise needs.
In today’s complex IT environments, organizations operate across hybrid infrastructures, cloud platforms, and distributed endpoints.
This creates a vast and ever-changing attack surface where manual monitoring and reactive defenses are no longer sufficient.
Enterprises need always-on protection that scales with their business — and that’s exactly what our Managed Security Services deliver.
We provide continuous monitoring, rapid detection, and proactive defense across your entire IT ecosystem.
By integrating advanced technologies with expert operations, we ensure compliance with global standards, streamline audit readiness,
and strengthen your overall security posture — without the overhead of building and maintaining an in-house SOC.
With 24/7 coverage, intelligent automation, and proven frameworks, our Managed Security Services deliver the confidence and control your organization needs to operate securely at scale.
Cybersecurity maturity is achieved through more than technology — it requires clear governance, disciplined risk management, and continuous compliance.
As regulatory frameworks evolve and threats grow more complex, enterprises must regularly evaluate their defenses, validate security controls, and ensure policies align with international standards.
Our Consultancy & Assessment Services provide the expertise and methodologies to achieve this balance.
We partner with organizations to identify vulnerabilities, assess risk exposure, and implement structured frameworks that strengthen resilience and meet both business and regulatory objectives.
From cloud and application security reviews to full compliance programs, we deliver the strategic insight and actionable recommendations needed to build a secure, compliant, and future-ready enterprise.
Selecting the right security partner is not just about tools — it’s about gaining the expertise, intelligence, and resilience needed to stay ahead of attackers.
Our SOCaaS is built to deliver more than monitoring; it provides a
holistic defense model that combines advanced technology, automation, and human expertise to protect your enterprise end to end.
With continuous coverage, AI-driven insights, and compliance-ready frameworks, we ensure your organization remains secure, agile, and cost-efficient, no matter how complex your environment becomes.
Cybersecurity is no longer just an IT function — it is a strategic enabler of business resilience, trust, and growth.
By integrating our SOCaaS into your operations, you gain measurable improvements in detection speed, response efficiency, and overall cost optimization.
Beyond protecting systems, our services safeguard brand reputation, ensure compliance, and provide real-time intelligence that prepares your enterprise for both current and emerging threats.
The result is a stronger, more resilient organization that can operate with confidence in an increasingly complex digital landscape.
With Commercis solutions, businesses gain a fortified environment that proactively defends against ransomware and malware, ensuring data security, operational continuity, and peace of mind.
Our cybersecurity solutions provide you with a multifaceted approach to combatting phishing and social engineering attacks. Through advanced email filtering, comprehensive employee training, simulated phishing tests, and robust incident response mechanisms, you can significantly enhance your defences against these threats.
By leveraging Commercis cybersecurity solutions, businesses can significantly enhance their data protection and compliance efforts. From comprehensive threat protection and data encryption to streamlined compliance management and employee training, these solutions provide the tools necessary to safeguard sensitive information and maintain regulatory adherence. Ultimately, this not only mitigates risks but also strengthens customer trust and business integrity in an increasingly digital landscape.
Through advanced behavioral analytics, user activity monitoring, access control, and data loss prevention measures, organizations can effectively identify, manage, and mitigate the risks posed by insiders. By fostering a culture of security awareness and collaboration, businesses can create a robust framework to protect sensitive data and maintain a secure operational environment. Ultimately, these proactive measures not only safeguard against insider threats but also enhance overall organizational resilience in the face of evolving cybersecurity challenges.
Our cybersecurity solutions provide you with a robust framework to combat Advanced Persistent Threats effectively. Through advanced threat detection, continuous network monitoring, AI-driven analysis, and proactive incident response, your organizations can enhance the ability to identify and mitigate these stealthy threats. By leveraging cutting-edge threat intelligence and fostering a culture of security awareness, you can build resilience against sophisticated attacks that seek to infiltrate your networks.
As your business operate across multiple remote locations, Commercis cybersecurity solutions provide a comprehensive approach to securing sensitive data and mitigating risks. Through advanced VPNs, robust endpoint security, secure access protocols, continuous monitoring, and employee training, organizations can effectively safeguard their operations in a dynamic remote work environment. By prioritizing these security measures, you not only protect your information but also enhance your resilience against the ever-evolving landscape of cyber threats.
Commercis cybersecurity solutions provide essential frameworks for securing cloud environments. By addressing misconfigurations, enhancing data protection, managing access controls, and ensuring compliance, organizations can effectively mitigate risks associated with cloud vulnerabilities. With continuous monitoring, incident response planning, and employee training, Commercis empowers businesses to safeguard sensitive information and fortify their cloud environments against potential threats. By leveraging these comprehensive solutions, organizations can navigate the complexities of cloud security and focus on driving innovation and growth while maintaining a strong security posture.
As cyber threats are constantly evolving, with new attack methods emerging frequently means that the fast-paced change requires businesses to continuously update defences, adopt threat intelligence services, and conduct regular security assessments to stay ahead of attackers.